PRO LDAP AD
The server must have the PHP module for LDAP installed. It is added to the auto-installation, but if you see an error indicating its absence, install it on the server with the command:
apt install php8.0-ldap
To connect Totum to your LDAP server, fill in the ttm__ldap_settings table:
h_host— LDAP server hosth_port— LDAP server port. Usually389.If your internal network configuration has multiple domains on different hosts, these parameters are passed in an array in
h_domains_settings(see further) to a specific domain. If the parameter is passed inh_domains_settings, it will be used from there. If not, it will be taken from the general settings:h_host-›hosth_port-›porth_version-›versionh_ssl-›sslh_cert_file-›cert_fileh_bind_format-›bind_format[at|dn]h_login_param-›login_paramh_fio_param-›fio_paramh_email_type-›email_type[bind|param]h_email_param-›email_paramh_get_groups-›get_groupsh_group_param-›group_param
h_version— if the field is not filled,{"LDAP_OPT_PROTOCOL_VERSION":"3"}is used, but you can set custom PHP connection settings in key-value format.h_ssl— check the box if you need to verify the LDAP server's SSL certificate.h_cert_file— upload two.keyand.crtcertificate files if the LDAP server uses a certificate issued by a non-public certification authority.h_ldap_on— enable after configuring all parameters.Important! Do not enable until you have verified the connection's functionality.
h_domains_settings— domain settings (one or more)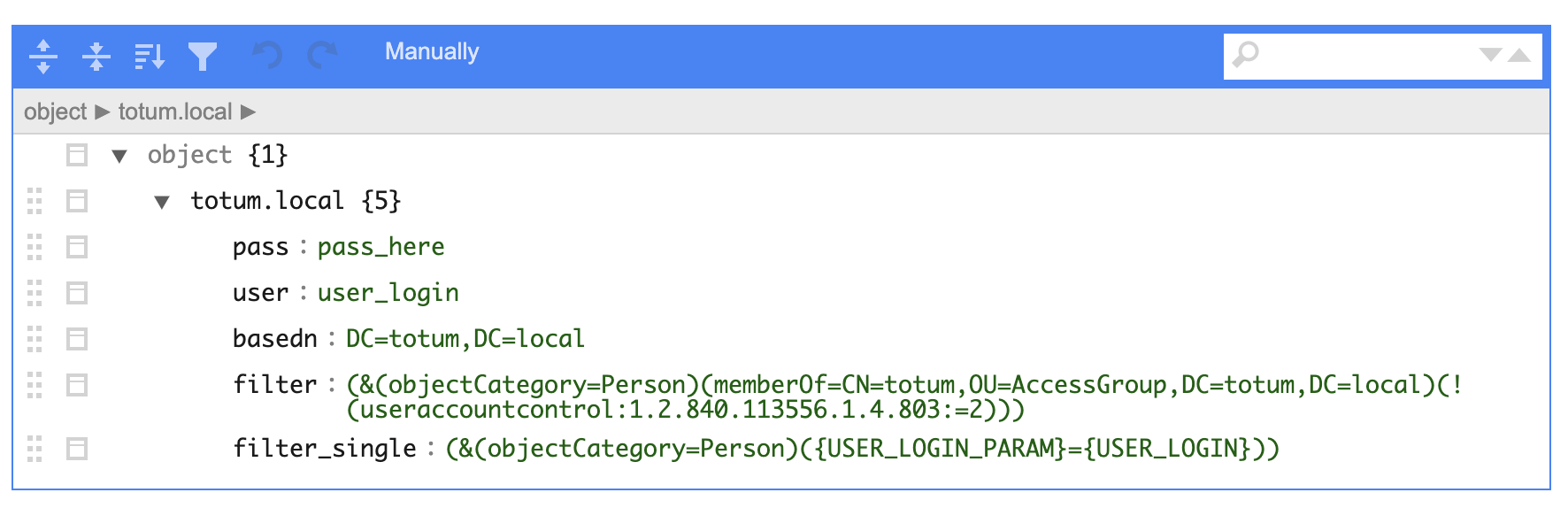
You can fill in the default example with the right button.
The domain is specified in the top key (fully with dots):
DC=totum,DC=local— should be specified astotum.localuser— the login of the user who has access to search in this domain.pass— the password of the access user.If the server supports anonymous requests,
userandpassmay be absent. They should be absent, not just empty!basedn— the baseDNwhere the filtering will be performed. If you don't know what this is, set theDNof the specified domain.For
AD, you cannot simply set theDNequal to the domain. Either a more specificOUwhere the search will be performed must be specified, or the parameter"LDAP_OPT_REFERRALS": "0",must be passed in theh_versionsfield. More details here.filter— the search filter based on which users will be selected from the LDAP server:// example for AD server (&(objectCategory=Person)(memberOf=CN=totum,OU=AccessGroup,DC=totum,DC=local)(!(useraccountcontrol:1.2.840.113556.1.4.803:=2)))// example for unix (uid=*)Documentation on search filters in AD: https://social.technet.microsoft.com/...
filter_single— the search filter by which a single user will be searched by their login:// for AD (&(objectCategory=Person)({USER_LOGIN_PARAM}={USER_LOGIN}))// for unix ({USER_LOGIN_PARAM}={USER_LOGIN})Two value replacements are used:
{USER_LOGIN_PARAM}— will be taken fromh_login_param.{USER_LOGIN}— will be the user's login.
h_bind_format— the format of user binding on the LDAP server:@ type— for AD serversdn type— for Linux servers (in this case, inh_domains_settings—domain—user]thednof the access user must be specified)
For
DN-type authorization, the modes of creating users “Load on first bind” inh_user_processing_typeare not available. Only preloading!h_domain_selector— the type of domain switcher on the authorization page (see further for the authorization sequence):Hidden
Totum/LDAP
Totum/Domain list
h_login_param— which parameter is the login on your password server.The standard value for AD is
sAMAccountName, which can be filled in with the right button.For Linux systems, it is likely to be
dn.
h_fio_param— what to record inFIOin the Totum users table. It can be changed directly in Totum. It will be updated fromLdaponly if this parameter changes inLdap.emailtype for recording in the Totum users table:From bind: login@domain.zone— the email will be formed from the login and domain.From param— the email will be taken from the parameter on the LDAP server specified inh_email_param.In both cases, the
emailcan be changed directly in Totum. It will be updated fromLdaponly if it changes inLdap.
h_show_result— checks the connection with the entered values. You can get data from the Ldap server considering the group search parameters with the right button.h_user_processing_type— determines when users will be created in Totum:Load on first bind — users will not be pre-created in Totum, only at the moment of successful binding.
Load on first bind with role matching — the user will be authorized and created in Totum only with a successful bind and role matching.
All found users — users will be loaded and created in Totum when
h_import_usersis pressed, regardless of role matching. If there is no role match, such users will have empty roles.Only with matching roles — users will be loaded and created in Totum when
h_import_usersis pressed only if they have matching roles.
h_get_groups— group retrieval settings. Additional requests will be made for each user with the substitution of{USER_DN}, and the result will be placed in the specified key (for AD, it can be filled in with the right button):Empty— do not load groups.get direct group membership:
groups: (&(objectCategory=group)(member={USER_DN}))- get indirect group membership (for cases where groups are nested within groups):
all_groups: (&(objectCategory=group)(member:1.2.840.113556.1.4.1941:={USER_DN}))h_group_param— the parameter that will be requested when performingh_get_groupsand by which group matching will occur. For AD,CNis usually used.h_import_users— imports users (adds and updates) from Ldap to Totum according to the settings.Features of creating a user in Totum
The Totum login for ldap-users is empty.
The value ldap is set in the ttm__auth_type field.
The login in ldap in the format loginParam@domain.zone is recorded in a separate field ttm__extparams (data type) + DN and loaded parameters are also recorded there + roles assigned according to the matching rules.
h_update_one_user— adds and updates a single user.h_generate_cron— creates a cron job in the Crons table, which presses theh_import_usersbutton according to the schedule.
Role Assignment Parameters in Totum
In comparison_parameters, parameters are collected, and in roles_in_totum — the corresponding roles in Totum.
Rules:
Results for each row will be summed up. If the user's parameters match several rows, they will receive the sum of the roles.
In
comparison_parameters:The key specifies the parameter by which the comparison is made.
If the parameter is a string, the comparison will be made by the full value.
If the parameter is a list, the comparison will be made by individual elements, separated by commas in the
Ldapresponse.For group parameters, the comparison is always made by individual elements, even if specified as a string value for the entire parameter.
All conditions are processed based on the
ANDprinciple (all specified parameters must be present).Keys are case-insensitive.
Values are case-sensitive!
Examples:
User dn + role Creator:
dn=cn=polunin,ou=Totum,dc=totum,dc=online
{
"dn": "cn=polunin,ou=Totum,dc=totum,dc=online"
}
Belongs to the domain totum.online and direct membership in the group Totum:
{
"dn": [
"dc=totum",
"dc=online"
],
"groups": "Totum"
}
Direct membership in the group totum and managers:
{
"groups": [
"Totum",
"Boss" ]
}
Direct membership in the group managers and indirect in totum:
{
"groups_all": "totum",
"groups": "managers"
}
Authorization Sequence
If
Ldapis enabled and if there is an@in the entered value, then check byemail.If this
emailbelongs to anLdapuser, then the authorization is sent to bind to the ldap-server.If the email is not found, then search in
ttm__extparamsby login + domain.If the selector is in the display state, and the domain after the at sign matches one of the domains, the selector will switch and remember for the next authorization in the browser.
If only the login is specified, then we look at the selected domain in the selector and search again in
loginor inttm__extparams.If the selector is in the Hidden status and only the login is specified, then first search in logins, and if not found and we have one domain in the list, then substitute this domain and search in
ttm__extparams.Login(those Totum users) in this case have priority.If there are multiple domains in the list, then we say that it was not found and do not go further.
If we did not find the user in Totum, then we will search for them in
Ldapunder the access user.If not found in
Ldapeither, then "User not found".If found, we create them and try to bind them.
If there are no matching roles and the setting is "Only with matching roles" — "User does not have access to Totum".
If the bind fails — "Authorization unsuccessful".
Stunnel as a Proxy from Client to LDAP Server
This instruction is taken from Google documentation.
Using Stunnel as a proxy server.
If the client does not provide a way to authenticate to LDAP using a client certificate (or for some other non-standard reasons, a secure connection to your LDAP server does not work), use the Stunnel service as a proxy server.
To do this, you need to configure Stunnel to provide the client certificate to the LDAP server, and in the client — connect to Stunnel. It is advisable to run Stunnel on the same server as your application and perform local listening (so that the LDAP directory is not accessible outside this server).
Install Stunnel:
apt-get install stunnel4
Create the configuration file /etc/stunnel/google-ldap.conf with the following content (in the example below, ldap-client.crt is the certificate file, and ldap-client.key is the key file, this is an example of connecting to Google AD):
[ldap]
client = yes
accept = 127.0.0.1:1636
connect = ldap.google.com:636
cert = ldap-client.crt
key = ldap-client.key
To enable Stunnel, open the file /etc/default/stunnel4 and set the parameter ENABLED=1.
Restart Stunnel:
service stunnel restart
Configure the application to point to ldap://127.0.0.1:1636.
If you also changed the accept line in the configuration file, you can replace 1636 with any other unused port number. Since the data exchange between the client and the Stunnel service occurs locally, the LDAP credentials are stored as plain text (the StartTLS/SSL/TLS parameter is disabled).
